Fortify Your Access with Endpoint Security Controls
Prevent and block cybersecurity threats arising out of the endpoint that as an entry point to enterprise resources
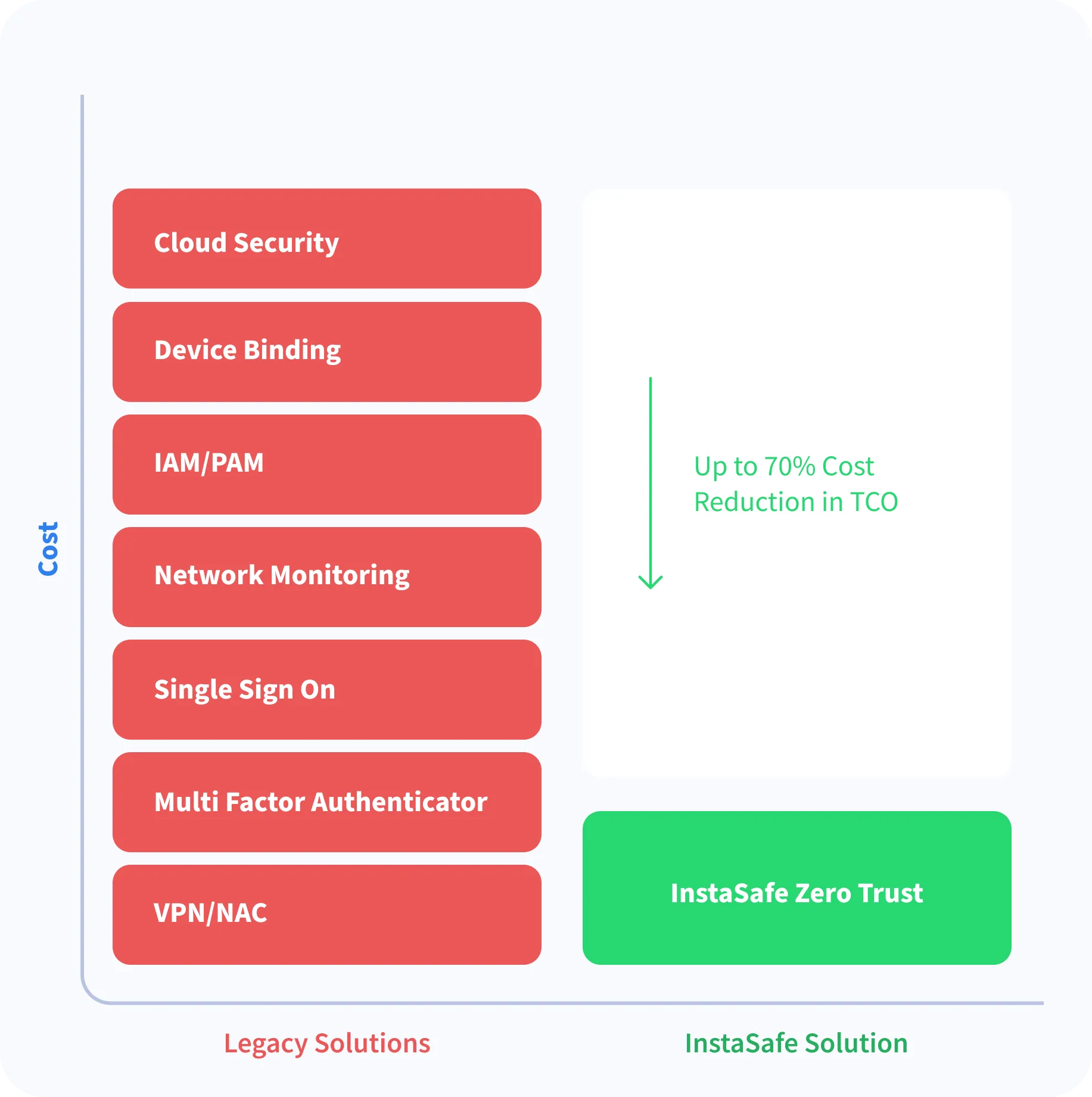
What is Endpoint Security control?
Endpoint security control is a core component of Zero Trust security model which secures application access and prevents data leakage with various control mechanisms. Endpoint is the entry point for enterprise network and resources. Having better security controls at endpoint can help IT administrator prevent a large number of threats
Endpoint Control Features and Capabilities

Clipboard Controls
Prevents the user from performing actions such as Copy & Paste, Screen Capture, Screen recording and clipboard access

Watermark Protection
Display the watermark logo and text as a graphical overlay over the content displayed on the screen.

Network Filter
Allows IT administrators to block specific domain URL or IP addresses from accessing by user or user groups

App Filter
Allows IT administrators to block end users from accessing specific applications installed on their devices

Chrome Control
Restrict users using Chrome browser from performing file downloads, opening developer tools, and taking print copy of the browser content.

Inactivity Timeout
Disconnect ZTNA agent in case there is no activity performed for a certain period of time or there is limited data transfer activity performed for a certain period of time.
Benefits of Endpoint Security Control
Data Loss Prevention
Prevents business critical data from being stolen or damaged by compromised endpoint devices.
Secure Remote Working
Remote workers are ensured that the data is accessed through secured way and critical data is not stolen or stored on local machine.
Protection against data breaches
Ensures that data is always being handled securely either by internal employees or third party workers, while protecting data breaches from threats arising from the endpoint.
Improved Compliance
Achieve better compliance with regard to how data is being accessed, stored, and protected.
Our Customers Say on 





Hariharan S
Vice President
"Good to use, easy to manage Zero Trust VPN security tool for cloud and ERP applications"
InstaSafe has been instrumental in supporting the Information Management strategy of my organization by providing a secure foundation for our hybrid network infrastructure. We have managed to easily extend always-on connectivity and secure access to our cloud and ERP applications with Instasafe Zero Trust Access. It is much faster than a VPN and much easier to manage.
